SSO Server
Communications
 |
Communications Settings
Compatibility (All XA Client versions)
By default, there are two communications ports utilized by the ExactAccess Server.
Listening Port
Port 15000 is used for the compatibility communications port. This facilitates communication and support of XA client versions prior to 4.5.650. For new installations, or installations where XA client version 4.5.650 or higher is deployed, this port can be disabled (recommended) if the clients have been configured to use the Indy protocol.
Tip
If you have deployed matched client versions (that are of the same version as the server), uncheck the box "Listen Port Enabled" under Compatibility (All XA client versions) to disable port 15000. This may also be unchecked of all of your client workstations are 4.8 or above.
Advanced (XA client versions 4.8.3 and above)
Listening Port
Port 15001 is used as the port for ExactAccess clients that dynamic protocol negotiations. If this port is updated on the server, a corresponding update must be made to the client workstations using this server.
Communications Thread Pool Limit
This protocol allows for selecting the thread cache limit for connections to help improve performance. The default 200 is sufficient for most installations, but can be configured as needed in high load environments, or may be lowered for low load environments. The number specified here means that the server will (pre)allocate this number of threads in the server process to handle incoming requests.
Local Server Management Port
This is the port bound to only the local address (127.0.0.1 or ::1) that the ExactAccess Server Monitor tool will use to query server status of the service.
Connection Hash Class
The available options are MD5 and WHIRLPOOL.
MD5 is a lightweight hash algorithm that generates 128 bit hashes, but is only recommended if the client workstations connecting to the system are slow (less than 2GHz).
WHIRLPOOL is a hash algorithm that generates 512 bit hashes. The larger number of bits means it is more secure, but it also requires slightly more CPU cycles to generate. WHIRLPOOL is the recommended choice if your workstations are 2GHz or better.
Warning
Not all HealthCast products support the Whirlpool hash algorithm. Ensure that the client product you are deploying supports the feature configuration for the server.
Database
 |
 |
Database Settings
Database Class
The only available database provider for this version of ExactAccess server services is FireDAC. It provides connectivity to Microsoft SQL Server using Microsoft Native Drivers or Microsoft SQL ODBC drivers.
Connection Timeout
This indicates how long the drivers will wait for a successful connection to a SQL server. If this ExactAccess installation will be using service database fail-over connection strings (multiple database connection strings are configured for the service), this number should be set as low as possible to improve fail-over responsiveness to secondary connections. For high availability configurations (SQL clustering, Active Group Listener configurations), this number should be set high enough for the drivers to allow clustering fail-over logic to promote a SQL server to the active state when the primary server has failed and not immediately return a connection failure to the service.
Command Timeout
This indicates how long any single transaction made by the service can take to complete. For highly stressed SQL servers, this number should be configured to allow for the appropriate workload to be completed even if the server is at maximum capacity. If there is excess capacity on the server, all service operations are expected to take less than 10 seconds to complete for normal operations.
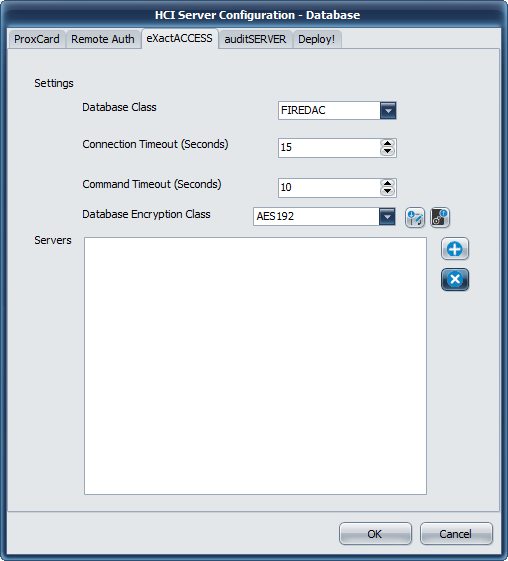
Database Encryption Class
For those server services that support updated database encryption, choose an encryption method to use to protect the data. During upgrades, choose the LEGACY or PROX_LEGACY option. After upgrade has been completed for all servers, choose a method other than LEGACY or PROX_LEGACY. AES192 is recommended, but any of the other options are valid. Consult your security officer for recommendations for your organization.
Important
During an upgrade scenario, the first server to be upgraded should be considered the "master" server. From this server, click the EXPORT button to save the auto-generated database encryption keys for each of the services (SSO and Prox) and save them to separate files (ProxDBKeys.key and XADBKeys.key) - provide a password to protect these files when prompted. It is a good idea to have more than one person export these keys, and keep them in a secure offsite location for disaster recovery.
Once these keys have been exported, they will need to be imported on each of the servers during the upgrade.
To import the keys to an existing server, Open the configuration tool, select Database, then choose the appropriate TAB (Prox or SSO/ExactAccess). Click the IMPORT button. Locate the correct file (ProxDBKeys.key for ProxCard, XADBKeys.key for SSO/ExactAccess keys) and click OK to open the file. Provide the password used to secure the exported keys. A message will indicate the success or failure of the import. Repeat this step for each server to be upgraded.
Servers
This lists the currently configured connection string for each configured SQL server in the organization. The ExactAccess server services support as many fail-over connection strings as desired. The first connection string entered in this list will be considered the primary server. The remaining servers listed will not be utilized unless the primary server Connection Timeout is reached and the server is deemed off-line. In primary server fail conditions, each of the servers will be attempted in the order in which they are entered in this list until a connection is made or all servers have been attempted and an error is returned to the client.
Adding a new connection
Click the plus ( ) button to bring up the Data Link Properties (FireDAC) window
) button to bring up the Data Link Properties (FireDAC) window
 |
Connections
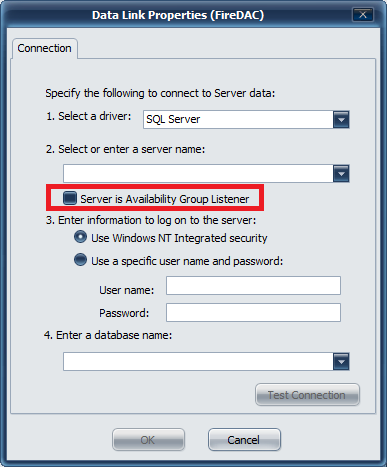
Select a driver
Microsoft provides several connectivity drivers for SQL server. You may choose SQL server as the driver (which is available by default on Windows 2012 R2 and above) - or optionally, install one of the later Microsoft SQL Server Native Drivers which will provide other connectivity options (such as ODBC)
Info
it may be necessary to install the Native SQL drivers. This is typically only necessary for Windows 2008 R2, but newer SQL drivers may also improve performance. See the note below on downloading an appropriate driver.
Driver Download
Check with the Microsoft Site for newer or additional drivers for supporting the latest versions of SQL server.
Select a server (by using the browsing service) or manually enter a SQL server database name and instance.
If this SQL server is part of the High Availability Group configuration (available in SQL server 2012 and above), check the box for Server is Availability Group Listener. This will notify the Microsoft Driver to expect multiple IP addresses from multiple SQL servers configured in this group/cluster so that the driver can provide appropriate fail-over if the primary node fails.
Authentication Type
If the service has been configured to run under a service account, that service account must have been granted DB Owner permissions for the service database (SSO, Prox, Deploy, Audit) when choosing to use Windows NT Integrated Security. In this case, a password does not need to be supplied in this configuration, as the security credentials are configured on the service using MMC services management tools provided by Windows.
Warning
When choosing to use Windows NT Integrated security during configuration, please note that the user account to launch the tool MUST match the account that is to be used for authentication to ensure the proper permissions and connectivity tests can be completed. The tool also requires UAC elevation, so this user must also be a local administrator on the server for configuration to be completed.
If you choose to use SQL server authentication, then pick the "Use a specific user name and password" that has been configured in SQL server as the DB owner of the service database (SSO, Prox, Deploy, Audit). This username and password will become part of the connection string and will be stored encrypted in the registry.
Enter a database name
Manually type if the name for the database associated with this service, or click the drop down to show a list of available databases to connect to.
Warning
If the current user (that the tool is running under) does not have access to the SQL server, the browse function will fail, as the tool is unable to connect to the SQL server with the current user. This is only applicable when using Windows NT Integrated Security.
When using SQL server authentication by supplying a user name and password, the browse feature for the database will only fail if the user has not been granted access to any databases, or the account information is not valid.
Other
 |
Directory Service Options
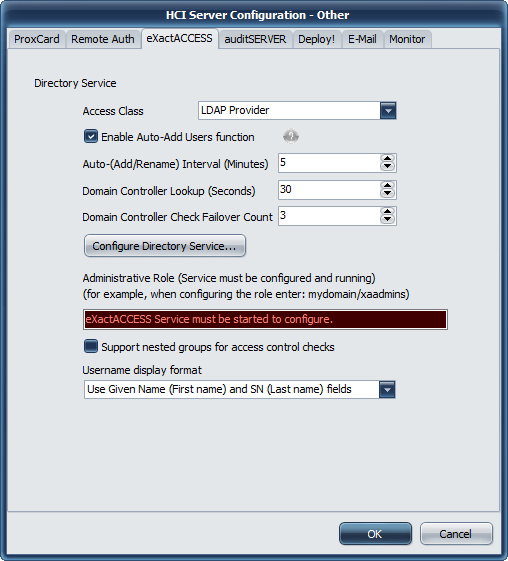
Access Class
Required
Before configuring settings on this page, it is required that the database configuration be completed and functional. The administrative role cannot be set if the database is not available.
Using the drop down, select the type of LDAP connection that the ExactAccess server will use to provide directory service services.
LDAP Provider — the basic LDAP provider used to request information from the domain controllers. This provider will display UNIVERSAL groups. LDAP is intended to reduce the network bandwidth required for directory communications. LDAP does not allow anonymous connections, therefore, the ExactAccess server must be configured to run under a domain account that has permissions to read the directory.
LDAP Global Catalog Provider — similar to the LDAP provider (it has the same limitations); this provider uses a Global Catalog Server for user and role lookups. For very large organizations with multiple domains within a forest, a global catalog is used as a cached data store of all domain "trees" within the "forest" of an Active Directory. It provides improved performance over the LDAP Provide when the domains are across WAN links. This makes it the ideal choice for multi-facility integration where each site maintains their own domain that is part of the same forest spanning multiple locations. All domains should have two way trusts and replicate their user and role information into the global catalog so that each domain data set is available on every global catalog server in the forest. If a user lookup in the global catalog fails, a fallback lookup using standard LDAP will be performed against the user account domain server(s). Note that the global catalog will only contain UNIVERSAL group membership information for accounts that are not part of the domain the GC is hosted on. This means that only UNIVERSAL groups may be used when assigning access permissions with this multi-site configuration.
Enable Auto-Add Users function
Select the Auto-Add Users radio button only on the primary server. For secondary server configuration, select Auto-Rename Users. The Auto-Rename Users option keeps the domain data cache synchronized with updates to Active Directory. This operation is also performed on the primary server when selecting the Auto-Add Users option.
Info
In a load balanced environment (with SQL server installed, and fail over configured on the same server), the primary database server should be configured as the Auto-Add server.
When using a SQL cluster that is not installed on the XA server there is no distinction between primary and secondary servers. In this case, you can choose any single XA server instance to perform the Auto-Add Users function. That server will be designated "Primary" for discussion purposes only.
Auto-(Add/Rename) Interval (Minutes)
Adjust the interval that the cache is synchronized on the server. The interval specified here indicates how long to wait between the synchronization operations (from the end of one, to the beginning of the next) To reduce network traffic, and load on the Directory Controller servers, increase this value to an appropriate interval. Keep in mind that an auto-add operation will be somewhere after this interval at a minimum before the user will be available in the ExactAccess database and be eligible for searching/finding with the XA HelpDesk tool.
Domain Controller Lookup (Seconds)
Occasionally, domain controllers need to be rebooted. When this happens, ExactAccess is designed to detect this based on how often it should validate the DC.
Domain Controller Check Count
The option for Lookup is how often to validate the current server to determine its operational state, and the Check Count is how many attempts the server will perform before it assumes the server is down (in the event an error is received during a user request/operation) The default values typically do not need to be changed.
Note
The domain controller checks are performed by querying the remote servers time. The server service must be configured with a user account that has permissions to make this query. If NetRemoteTOD has been blocked or the user does not have permissions to make this call to the domain controller, XA will not be able to determine the operational state and will disable access to the domain controller.
New for 4.11
Domain controllers are processed in round robin order when queries to the domain are performed on behalf of the user. This spreads the user requests across all domain controllers rather than sending all requests to a single server as previous versions of the XA server performed.
Exclude DC(s) from the round robin processing
To exclude one or more DCs from being utilized,
Open Regedit
Navigate to Software\HealthCast\ExactAccess\XADSNT\Servers\<domain>
<domain> will be the NETBIOS name of the domain configured as shown below in Configure Directory Service
Create or add to the comma separated list in the value ExcludedDCs: reg_sz
A service restart will need to be performed after adding exclusions
Example:
Software\HealthCast\ExactAccess\XADSNT\Servers\BOISETESTAD
ExcludedDCs=DC01,DC02
Tip
There are several reasons to exclude DCs from the round robin processing:
Windows domain controllers are stored in AD, so a query to AD for domain controllers will return all records, even to DCs that are no longer present (may have been improperly removed from the domain/forest), or not powered on.
DCs may be located across a slow link such as a WAN, so to improve performance, exclude DCs that are not on the current network.
Under-powered DCs may have problems processing the user or role lookup queries that XA performs. If a DC returns errors (these would show as warnings or errors in the NT Event log indicating the DC failure) the DC should be excluded.
Query Domain Controller List
nltest /dclist:<DomainName>
Info
For additional details on the NLTest command, see the Microsoft Technet article
Disable Internal Directory Service Cache
The following registry key/value can be used to disable cache:
Open
RegeditNavigate to
HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\XADSNTAdd the following registry value:
isInternalCacheEnab led: reg_dword = 0
Note
If the key/value is not present, caching is enabled.
If the value is set to 1, caching is enabled.
If the value is set to 0, caching is disabled.
Configure Directory Service
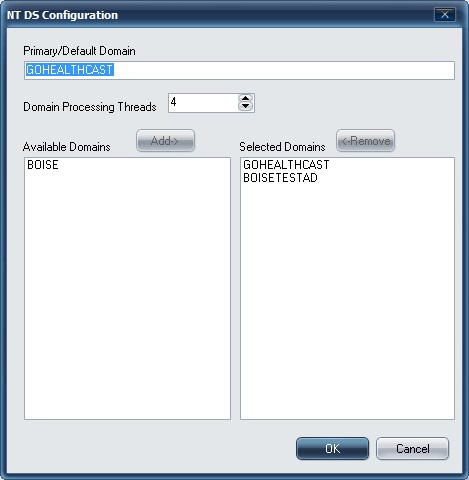
Once the configuration class has been chosen, the server must be configured with the domains that will be SSO enabled. The configure directory service button is used during initial configuration of the server to select the domain or domains that will be linked to the ExactAccess server.
Info
The "computer browser" service may need to be enabled and running for this application to find the domains. If this service is stopped or is not started, the domains view may be blank.
Warning
If any of the domains show as "dotted DNS names" instead of the short names as shown above, ExactAccess must be configured to use DNS lookup.
Cancel the dialog, and stop the ExactAccess Service.
Open Regedit to the following registry key and set the value to 1
HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\XADSNT\Servers
useDNSnames: reg_dword = 1
Restart the service, then restart the configuration tool.
When you have selected to add a domain to the window on the right, double click that domain to select it as the primary domain.
The Domain Processing threads value is used to determine the number of work threads available for domain communications. It is recommended that 2 threads be allocated per domain added to the list of selected domains up to the processing core count available on the server. If fewer domains are selected than half the work threads, the remaining threads are simply not used, and do not impact system performance.
Example
If 3 domains are selected, the count would be 6 threads, however, if only 4 processing cores are available (2 cores + 2 hyper threads, or 4 cores with no hyper threading), then the recommended value is 4.
After selecting the appropriate domains and pressing the OK button, the system will perform a SID lookup. The SID is a security ID associated with the domain, and is a base for all user and role accounts to provide a unique id to each object. XA will cache the domain SID to improve performance for certain operations.
Note
In order for this operation to complete successfully, the configuration tool must have been started under a domain account that has read permissions to each of the selected domains. This is especially important if full, two way trusts do not exist between the server domain and any of the selected domains.
Once the configuration of the domains is complete, click the OK button to commit the configuration.
The service must now be restarted. Using the Service Control Manager (SCM) Stop (if it was previously running) and (Re)Start the HCI ExactAccess Server service.
Nested Groups
The LDAP and LDAP+GC (global catalog) Providers allow ExactAccess to support nested group membership for user access control. This feature requires that the Active Directory version be Windows 2003 SP2 or higher. If you would like to support nested groups in your environment, ensure the Support Nested Groups for access control checks is checked.
Caution
Using nested groups can have a significant performance impact on user login times. Evaluate whether this option is necessary before enabling it.
User Name Display Format
This corresponds to how to parse and display user names as provided by the directory service. It is recommended that the Use Given Name (First name) and SN (Last name) fields option be chosen. This setting affects the privacy shield display name settings.
Tip
Use Display name option is intended to be a compatibility layer for upgrading XA server from previous versions that supported the WINNT access method where this was the only display option supported by the access class. This version of ExactAccess no longer supports NT Authentication, but it can still be configured to use the old field for display purposes.
Info
The final step is to configure the Administrative role. To complete this step, the service and the configuration tool must both be restarted.
The ExactAccess server must be restarted so that it can contact the configured domain controllers to read the user and role information for the configured domain(s). Once that operation is complete, the configuration tool can determine that the service is ready for the configuration of the primary administrators role/group to be set and saved.
The administrative role field will become editable once all other configuration has been completed. Enter the domain/role name for the primary administrative group from active directory.
